WooCommerce published an advisory about an XSS vulnerability while Wordfence simultaneously advised about a critical vulnerability in a WooCommerce plugin named Dokan Pro. The advisory about Dokan Pro warned that a SQL Injection vulnerability allows unauthenticated attackers to extract sensitive information from a website database.
Dokan Pro WordPress Plugin
The Dokan Pro plugin allows user to transform their WooCommerce website into a multi-vendor marketplace similar to sites like Amazon and Etsy. It currently has over 50,000 installations Plugin versions up to and including 3.10.3 are vulnerable.
According to WordFence, version 3.11.0 represents the fully patched and safest version.
WordPress.org lists the current number of plugin installations of the lite version at over 50,000 and a total all-time number of installations of over 3 million. As of this moment only 30.6% of installations were using the most up to date version, 3.11 which may mean that 69.4% of all Dokan Pro plugins are vulnerable.
Screenshot Of Dokan Plugin Download Statistics
Changelog Doesn’t Show Vulnerability Patch
The changelog is what tells users of a plugin what’s contained in an update. Most plugin and theme makers will publish a clear notice that an update contains a vulnerability patch. According to Wordfence, the vulnerability affects versions up to and including version 3.10.3. But the changelog notation for version 3.10.4 that was released Apr 25, 2024 (which is supposed to be patched) does not show that there’s a patch. It’s possible that the publisher of Dokan Pro and Dokan Lite didn’t want to alert hackers to the critical vulnerability.
Screenshot Of Dokan Pro Changelog

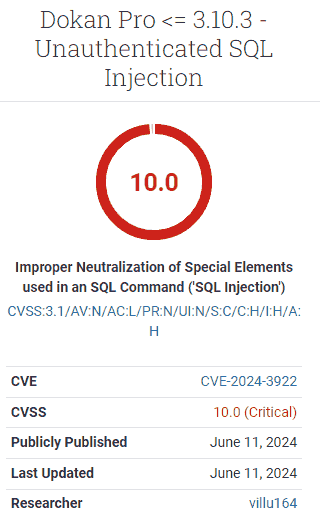
CVSS Score 10
The Common Vulnerability Scoring System (CVSS) is an open standard for assigning a score that represents the severity of a vulnerability. The severity score is based on how exploitable it is, the impact of it, plus supplemental metrics such as safety and urgency which together add up to a total score from least severe (1) to the highest severity (10).
The Dokan Pro plugin received a CVSS score of 10, the highest level severity, which means that any users of the plugin are recommended to take immediate action.
Screenshot Of Dokan Pro Vulnerability Severity Score
Description Of Vulnerability
Dokan Pro was found to contain an Unauthenticated SQL Injection vulnerability. There are authenticated and unauthenticated vulnerabilities. Unauthenticated means that an attacker does not need to acquire user credentials in order to launch an attack. Between the two kinds of vulnerabilities, unauthenticated is the worst case scenario.
A WordPress SQL Injection vulnerability is one in which a plugin or theme allows an attacker to manipulate the database. The database is the heart of every WordPress website, where every password, login names, posts, themes and plugin data. A vulnerability that allows anyone to manipulate the database is considerably severe – this is really bad.
This is how Wordfence describes it:
“The Dokan Pro plugin for WordPress is vulnerable to SQL Injection via the ‘code’ parameter in all versions up to, and including, 3.10.3 due to insufficient escaping on the user supplied parameter and lack of sufficient preparation on the existing SQL query. This makes it possible for unauthenticated attackers to append additional SQL queries into already existing queries that can be used to extract sensitive information from the database.”
Recommended Action For Dokan Pro Users
Users of the Dokan Pro plugin are recommended to consider updating their sites as soon as possible. It’s always prudent to test updates before their uploaded live to a website. But due to the severity of this vulnerability, users should consider expediting this update.
WooCommerce published an advisory of a vulnerability that affects versions 8.8.0 and higher. The vulnerability is rated 5.4 which is a medium level threat, and only affects users who have the Order Attribute feature enabled activated. Nevertheless, WooCommerce “strongly” recommends users update as soon as possible to the most current version (as of this writing), WooCommerce 8.9.3.
WooCommerce Cross Site Scripting (XSS) Vulnerability
The type of vulnerability that affects WooCommerce is called Cross Site Scripting (XSS) which is a type of vulnerability that depends on a user (like a WooCommerce store admin) to click a link.
According to WooCommerce:
“This vulnerability could allow for cross-site scripting, a type of attack in which a bad actor manipulates a link to include malicious content (via code such as JavaScript) on a page. This could affect anyone who clicks on the link, including a customer, the merchant, or a store admin.
…We are not aware of any exploits of this vulnerability. The issue was originally found through Automattic’s proactive security research program with HackerOne. Our support teams have received no reports of it being exploited and our engineering team analyses did not reveal it had been exploited.”
Should Web Hosts Be More Proactive?
Web developer and search marketing expert Adam J. Humphreys, Of Making 8, inc. (LinkedIn profile), feels that web hosts should be more proactive about patching critical vulnerabilities, even though that may cause some sites to lose functionality if there’s a conflict with some other plugin or theme in use.
Adam observed:
“The deeper issue is the fact that WordPress remains without auto updates and a constant vulnerability which is the illusion their sites are safe. Most core updates are not performed by hosts and almost every single host doesn’t perform any plugin updates even if they do them until a core update is performed. Then there is the fact most premium plugin updates will often not perform automatically. Many of which contain critical security patches.”
I asked if he meant a push update, where an update is forced onto a website.
“Correct, many hosts will not perform updates until a WordPress core update. Softaculous engineers confirmed this for me. WPEngine which claims fully managed updates doesn’t do it on the frequency to patch in a timely fashion for said plugins. WordPress without ongoing management is a vulnerability and yet half of all websites are made with it. This is an oversight by WordPress that should be addressed, in my opinion.”
Read more at Wordfence:
Read the official WooCommerce vulnerability documentation:
WooCommerce Updated to Address Cross-site Scripting Vulnerability
Featured Image by Shutterstock/New Africa

