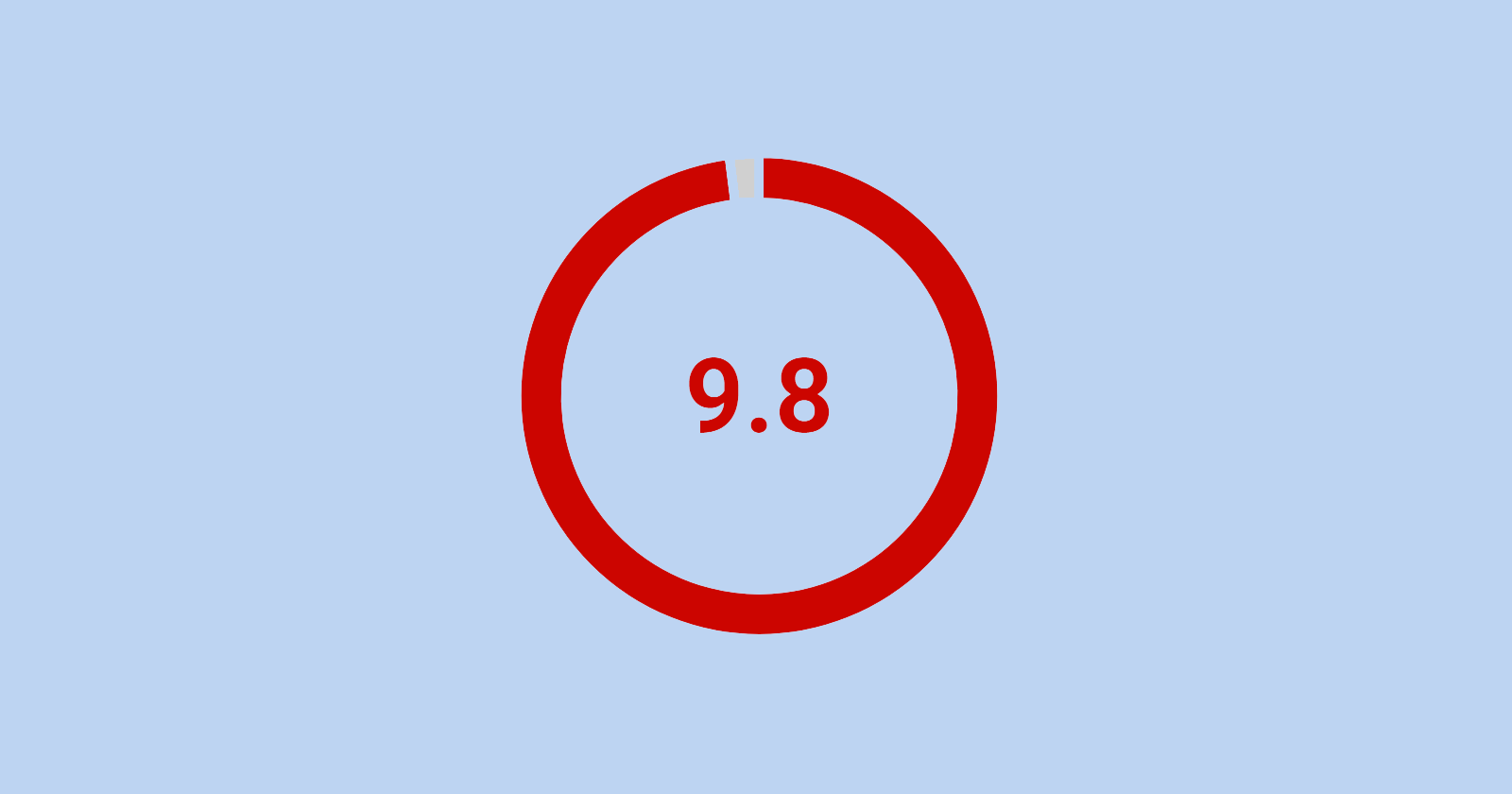
Bricks Visual Site Builder for WordPress recently patched a critical severity vulnerability rated 9.8/10 which is actively being exploited right now.
Bricks Builder
Bricks Builder is a popular WordPress development theme that makes it easy to create attractive and fast performing websites in hours that would costs up to $20,000 of development time to do from scratch without it. Ease of use and developer components for CSS have made it a popular choice for developers.
Unauthenticated RCE Vulnerability
Bricks Builder is affected by a remote code execution (RCE) vulnerability. It’s rated 9.8/10 on the Common Vulnerability Scoring System (CVSS), which is nearly the highest level.
What makes this vulnerability particularly bad is that it’s an unauthenticated vulnerability which means that a hacker doesn’t need to attain permission credentials to exploit the vulnerability. Any hacker who knows of the vulnerability can exploit it, which in this case means an attacker can execute code.
Wordfence describes what can happen:
“This makes it possible for unauthenticated attackers to execute code on the server.”
The details of the vulnerability have not been officially published.
According to the official Bricks Builder changelog:
“We just released a mandatory security update with Bricks 1.9.6.1.
A leading security expert in the WordPress space just brought this vulnerability to our attention, and we instantly got to work, providing you now with a verified patch.
As of the time of this release, there’s no evidence that this vulnerability has been exploited. However, the potential for exploitation increases the longer the update to 1.9.6.1 is delayed.
We advise you to update all your Bricks sites immediately.”
Vulnerability Is Being Actively Exploited
According to Adam J. Humphreys (LinkedIn), founder of the web development company Making 8, the vulnerability is actively being exploited. The Bricks Builder Facebook community is said to be responding to affected users with information on how to recover from the vulnerability.
Adam J. Humphrey’s commented to SEJ:
“Everyone is getting hit bad. People on hosts without good security got exploited. A lot of people are dealing with it now. It’s a bloodbath and it’s the number one rated builder.
I have strong security. I’m so glad that I’m very protective of clients. It all seemed overkill until this.
People on hosts without good security got exploited.
SiteGround when installed has WordPress security. They also have a CDN and easy migrations with their plugin. I’ve found their support more responsive than the most expensive hosts. The WordPress security plugin at SiteGround is good but I also combine this with Wordfence because protection never hurts.”
Recommendations:
All Bricks Builder users are encouraged to update to the latest version, 1.9.6.1.
The Bricks Builder changelog announcement advises:
“Update Now: Update all your Bricks sites to the latest Bricks 1.9.6.1 as soon as possible. But at least within the next 24 hours. The earlier, the better.
Backup Caution: If you use website backups, remember they may include an older, vulnerable version of Bricks. Restoring from these backups can reintroduce the vulnerability. Please update your backups with the secure 1.9.6.1 version.”
This is a developing event, more information will be added when known.